Knowledge Base
2025.10
GENERIC
Networking
Storage
Compute
Designate
Orchestration
Self-Hosted
Install
UPGRADE
Monitoring
Add-Ons
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
SSO got Disabled Post Management Plane Upgrade
Summarize Page
Copy Markdown
Open in ChatGPT
Open in Claude
Problem
- SSO appears disabled in the UI after upgrading the PCD management plane, but the backend SSO configuration is functioning correctly.
Environment
- Private Cloud Director - v2025.4 and v2025.6
- Self-Hosted Private Cloud Director - v2025.4 and v2025.6
- SSO
Cause
- The issue happened due to a bug (PCD-2029). After upgrading from the FEB release to the APR release, the "Enable SSO" flag appears disabled in the Enterprise SSO UI section, even though SSO is actually configured and functional (e.g., SAML group details are visible).
- The issue occurs because the signing attribute is not included when creating the SSO config, and fetching it later from Consul fails. As a result, the UI treats the SSO setup as incomplete and displays the "Enable SSO" flag as disabled. The bug is now fixed with v2025.7 release.
Diagnostics
- After upgrading the PCD management plane, navigate to Settings > Enterprise SSO in the user interface. The SSO feature will be disabled following the upgrade.
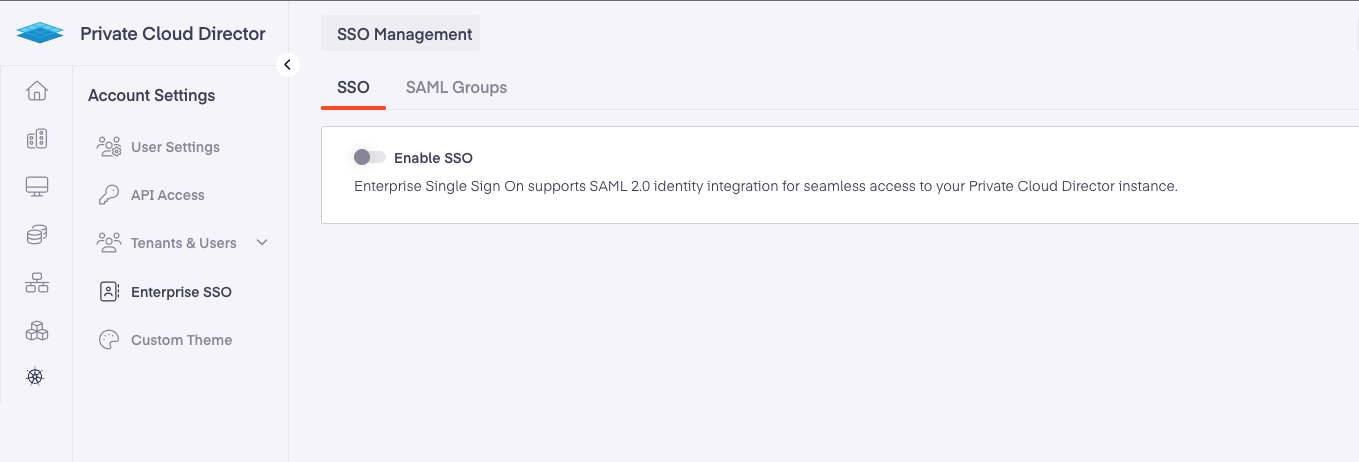
Workaround
- For PCD (SaaS), the platform9 support team will apply the steps below. Please open a Support Ticket.
- For Self-Hosted PCD (air-gapped), perform the steps below from the management plane cluster.
- Install consul CLI, refer this documentation.
- Get
hagriddeployment configuration.
Command
$ kubectl get deploy/hagrid -o yaml -n <INFRA_REGION_NAMESPACE> > hagrid-deployment.yamlSearch inside the
hagrid-deployment.yamlfile for below variables.CONSUL_HTTP_ADDRCONSUL_HTTP_TOKENCUSTMOR_ID
Export values into current shell session.
Command
export CONSUL_HTTP_ADDR="<CONSUL_HTTP_ADDR_FROM_HAGRID_CONFIG>" export CONSUL_HTTP_TOKEN="<CONSUL_HTTP_TOKEN_FROM_HAGRID_CONFIG>" export CUSTMOR_ID="<CUSTMOR_ID_FROM_HAGRID_CONFIG>"- Once the environment is configured, run the following command to store the signing flag.
consul command
$ consul kv put customers/$CUSTOMER_ID/keystone/sso/saml2/IDP1/signing falseValidation
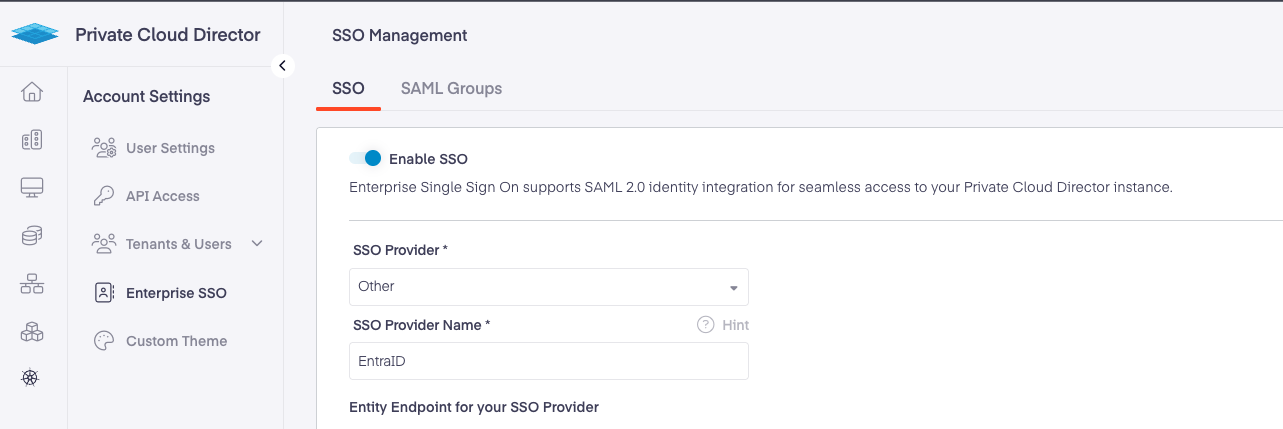
- Navigate to Settings > Enterprise SSO in the user interface. The SSO feature will be enabled.
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Discard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message